November 23, 2023
A Security Perspective on the GameFi Fren Pet Across the Entire Chain

After the hype around Friend.tech subsided, the blockchain game Fren Pet, built on the Base chain by two developers, has captured the market’s attention. From November 19th to 20th, thanks to the official support from Base and the social play of Fren Pet, it gained widespread attention on social media, becoming a rising star in the GameFi sector.
Despite the rapid growth in Fren Pet users, security remains a crucial aspect. Today, Beosin team will analyze the design mechanism and contract code of Fren Pet to help you understand potential risks.
Fren Pet Mechanism Analysis
The current gameplay of Fren Pet includes pet forging, feeding, pet battles with other users, a lucky wheel, and dice rolling. Users participating in Fren Pet need to forge pets (NFT) by spending 100 FP tokens. If other users forge pets later, the spent FP tokens are returned. Users then need to use FP tokens to buy items like apples and coffee to feed their pets, preventing the pets’ TOD (time of death) from reaching zero, which would automatically destroy the held NFT.
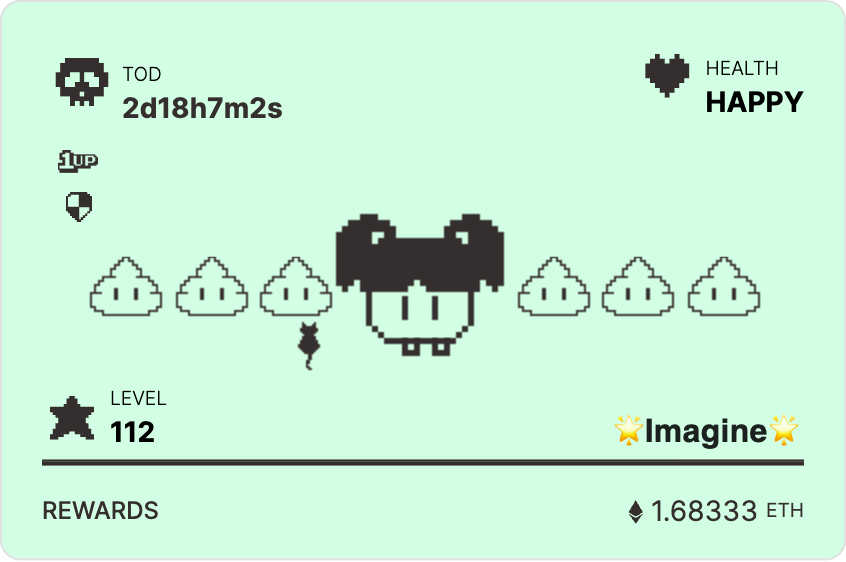
Feeding pets earns points (Pet Points), and the higher the points, the more ETH rewards users receive. The ETH rewards come from the transaction tax on FP tokens, with a 5% fee per transaction, of which 2% is distributed to game players. Therefore, the more users participate, the greater the demand for FP tokens, leading to higher transaction volumes and more significant ETH rewards.
Fren Pet Contract Analysis
Fren Pet Main Contract
The main contract address for Fren Pet is 0x85b157EbaAF289De5301aE6694B651BF3b8df1C3, with the NFT contract address being 0x5b51Cf49Cb48617084eF35e7c7d7A21914769ff1, and the token contract address being 0xFF0C532FDB8Cd566Ae169C1CB157ff2Bdc83E105. Through a scan using the Beosin VaaS tool and analysis by Beosin security audit experts, potential security risks have been identified in its contracts.
Suggestions to Enhance Contract Security
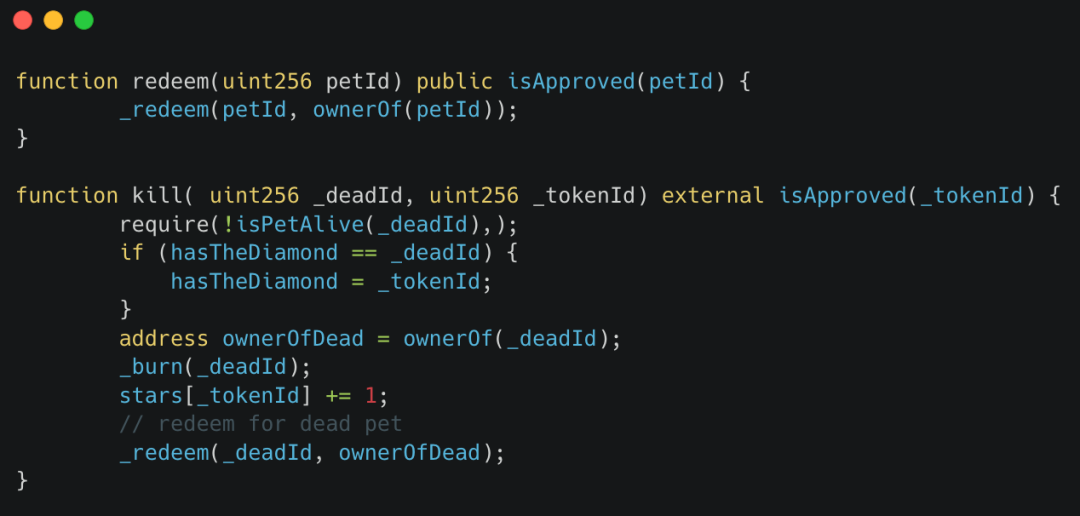
1. Add nonReentrant Modifier
In the redeem and kill functions of the contract, developers should ensure there is no risk of reentrant attacks. It is recommended to use the nonReentrant modifier from the OpenZeppelin anti-reentrancy contract to prevent reentrancy attacks.
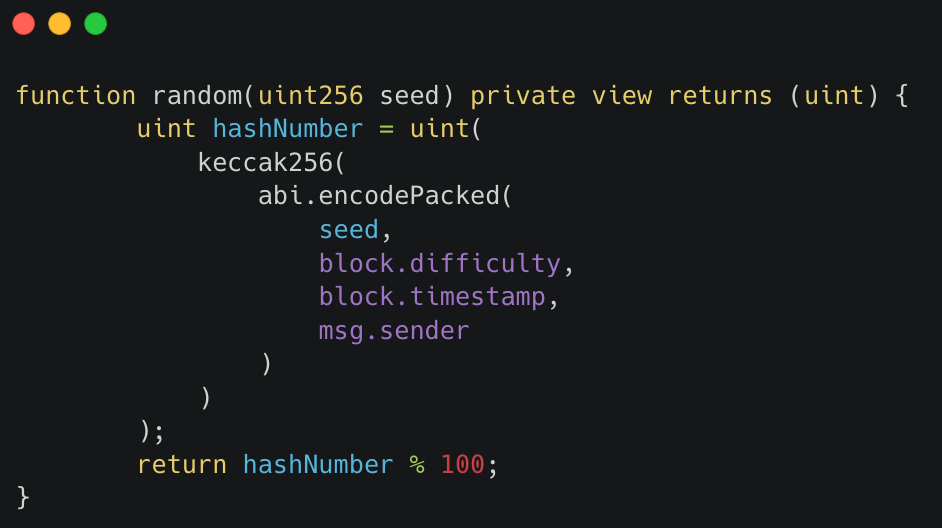
2. Use a Secure Random Number Generator
The Fren Pet main contract uses a random number generated from the block and sender address. A more secure approach is to use a reliable and fair random number generator like Chainlink’s Verifiable Random Function.
3. Pay Attention to Access Control
The Fren Pet main contract uses the isApproved modifier to control whether the caller has permission to invoke functions. Developers need to be extremely familiar with their project’s business logic and ensure that permissions cannot be bypassed. In the Fren Pet V2 contract, access control issues should continue to be prioritized.
This concludes the analysis and suggestions for improving the security of the Fren Pet main contract.
Fren Pet NFT Contract
The overall structure of the Fren Pet NFT contract is as follows:
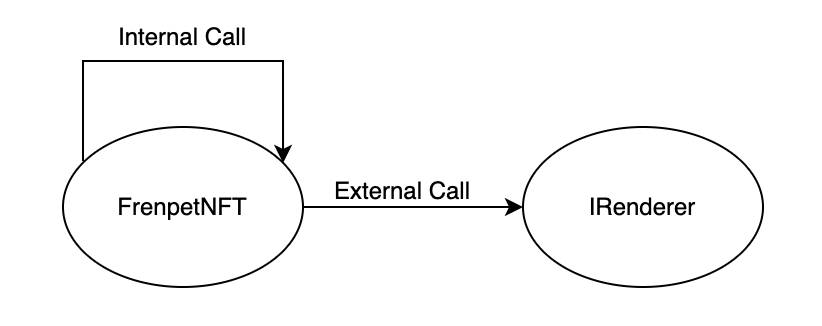
The FrenpetNFT contract inherits ERC721 and is responsible for the minting and burning of NFTs. The IRenderer is responsible for handling the metadata of Fren Pet NFTs. It is recommended to emit events when the setRenderer and setMinter functions are called so that external entities can listen and track the transfer of relevant information.

Fren Pet Token Contract
1. Centralized Risk
The token contract has multiple onlyOwner functions, such as the blacklist and updateBuyFees functions, which can significantly impact token transactions. The contract owner can modify transaction fees, prevent user buy/sell actions, and add blacklist addresses.
2. Lack of Timelock
The Fren Pet token contract lacks a timelock to restrict the contract owner’s operational authority. While some functions like withdrawStuckToken() and updateSwapEnabled() allow emergency measures to protect user assets, the absence of a timelock could potentially lead to misuse of these functions.
Beware of Phishing Risks
In addition to contract risks, the popularity of Fren Pet has led to numerous phishing websites and social accounts. Users are strongly advised not to click on fake links, especially those obtained from a Google search. It is recommended to verify links through other social platforms to avoid falling into phishing traps.
Users should remember some anti-phishing techniques, try to avoid falling victim to phishing scams, or consider installing the Beosin Alert anti-phishing plugin to help identify phishing websites.
Beosin Alert: https://chromewebstore.google.com/detail/beosin-alert/lgbhcpagiobjacpmcgckfgodjeogceji
Conclusion
While Fren Pet contracts do not exhibit obvious business logic vulnerabilities, there are apparent centralization risks, and certain code sections could have more secure implementations to enhance contract security. Given the market’s previous GameFi and SocialFi trends, ordinary users may experience FOMO emotions, blindly falling into phishing traps. Users need to recognize that Fren Pet is just a Web3 attempt by two developers. It is crucial for users to manage their funds and conduct project research, participating in a rational manner.
Contact
If you need any blockchain security services, welcome to contact us:
Related Project
Related Project Secure Score
Guess you like

Beosin Unveils New Blockchain Solution for Financial Regulation and Security at SFF
November 20, 2023

Heco Bridge hacked over $83M and Kyber exploited over $48M. How should we be more vigilant after these two security incidents?
November 24, 2023
Understanding the RGB Protocol: Bridging Bitcoin and Smart Contract
November 24, 2023

Unlicensed Exchanges Collapse - How Should Users Guard Against It?
November 28, 2023
