November 03, 2023
Analysis of $2.18 Million Loss in Hacker Attack on OnyxProtocol
On November 1, 2023, Beosin EagleEye detected that the oPEPE market contract of OnyxProtocol fell victim to a hacker attack, resulting in a profit of approximately $2.18 million for the hacker.
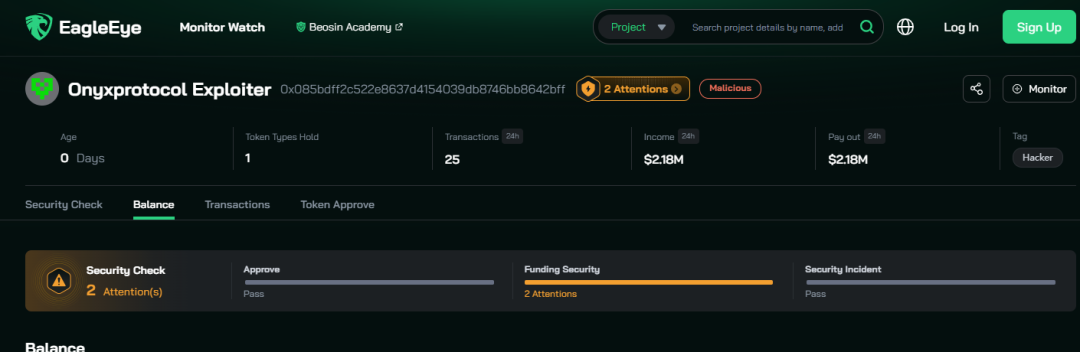
OnyxProtocol, a branch of CompoundV2, had previously witnessed a $7 million loss due to a similar vulnerability experienced by HundredFinance back in April 15, 2022. This analysis revisits that specific vulnerability.
Key Information
Attack transaction
0xf7c21600452939a81b599017ee24ee0dfd92aaaccd0a55d02819a7658a6ef635
Attacker address: 0x085bdff2c522e8637d4154039db8746bb8642bff
Attack contracts
0x526e8e98356194b64eae4c2d443cc8aad367336f
0xf8e15371832aed6cd2741c572b961ffeaf751eaa
0xdb9be000d428bf3b3ae35f604a0d7ab938bea6eb
0xe495cb62b36cbe40b9ca90de3dc5cdf0a4259e1c
0x414764af57c43e36d7e0c3e55ebe88f410a6edb6
0xcede81bb4046587dad6fc3606428a0eb4084d760
Attacked contracts
0x5fdbcd61bc9bd4b6d3fd1f49a5d253165ea11750
0x9dcb6bc351ab416f35aeab1351776e2ad295abc4
Vulnerability Analysis
The attack primarily exploited rounding and exchange rate manipulation, breaching the project's code defenses.
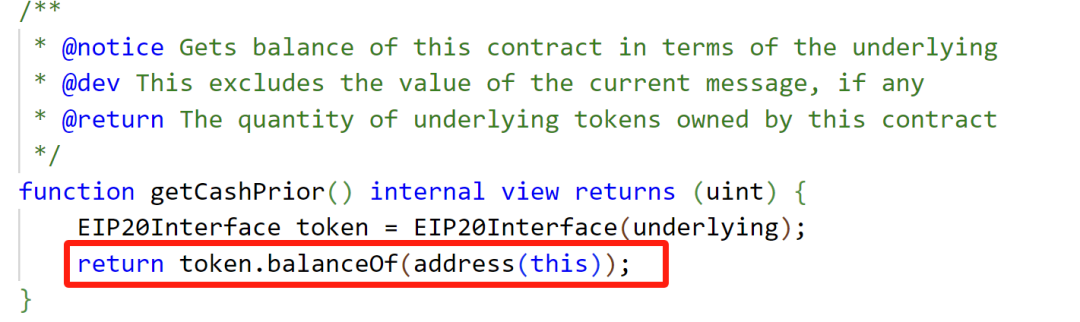
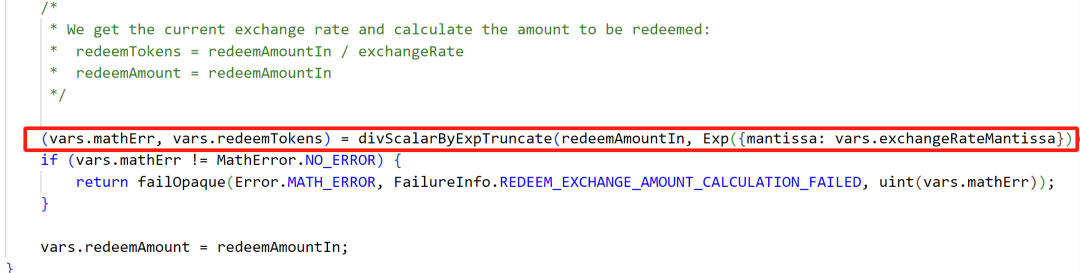
Attack Process
Preparation phase:
1. The attacker borrowed 4000 WETH as preparatory funds.
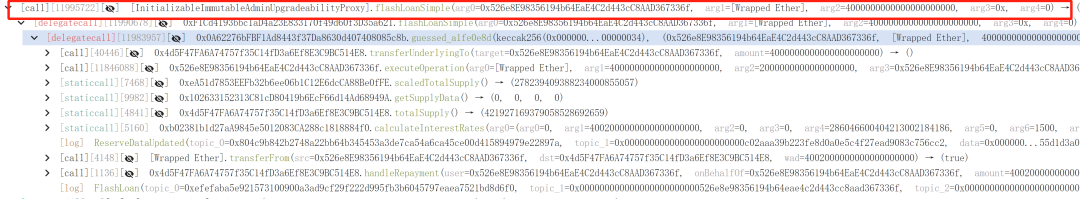
2. These funds were converted into roughly 2.52 trillion PEPE.
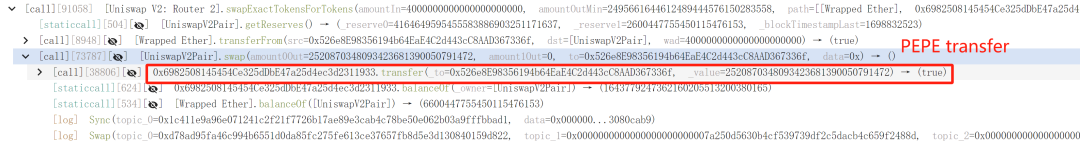
3. The 2.52 trillion PEPE was distributed among various addresses, completing the attack preparation phase.
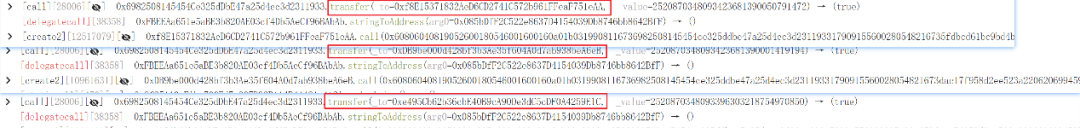
Execution Phase:
1. The attacker acquired a small amount of oPEPE and introduced PEPE into the oPEPE market, altering the PEPE balance and manipulating the exchange rate.

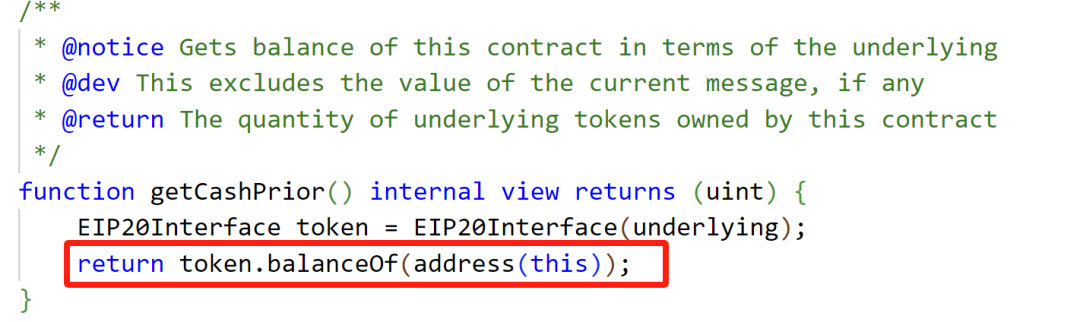
2. A substantial amount of Ethereum was borrowed maliciously from other markets.
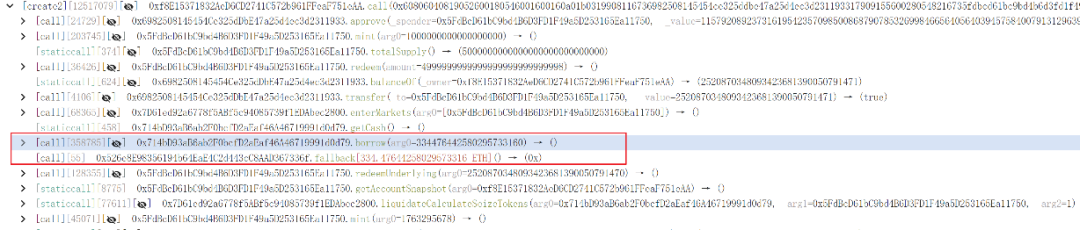
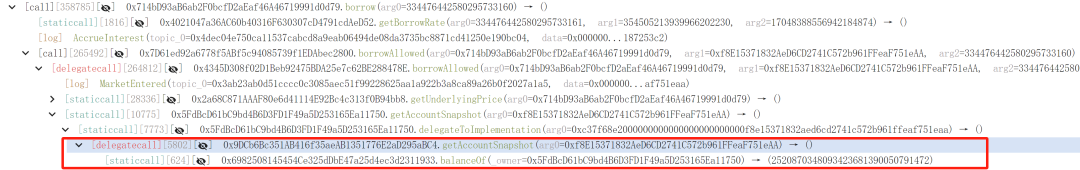
3. Leveraging rounding and rate manipulation, the attacker used a small oPEPE quantity to liquidate borrowing and reclaim contributed funds.
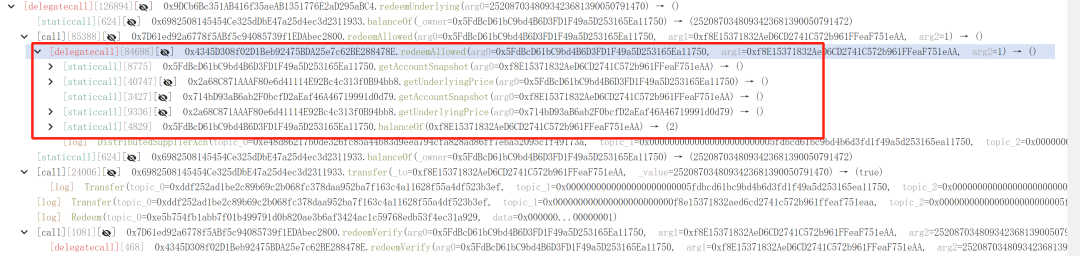
4. Repeating these steps, the attacker ultimately converted PEPE back to ETH, repaid the flash loan, and secured a profit of 1156 ETH.
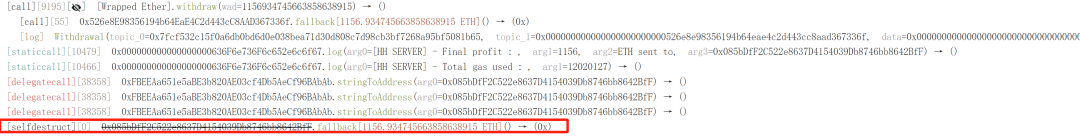
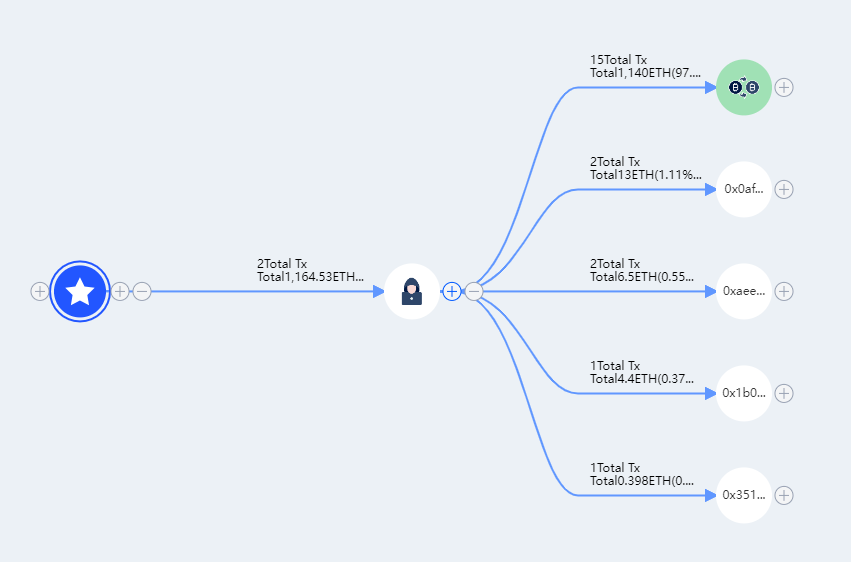
Fund Tracking
At the time of writing, Beosin Trace tracking discovered that the stolen funds had been entirely transferred to Tornado Cash.
Recommendations
Following this event, Beosin's security team advises the following measures:
1. Employ reserve ledgers to record asset borrowing situations.
2. Enhance precision to mitigate errors stemming from arithmetic operations.
3. Prior to project deployment, opt for a comprehensive security audit by a professional firm to mitigate security risks.
Contact
If you need any blockchain security services, welcome to contact us:
Official Website Beosin EagleEye Twitter Telegram LinkedIn
Related Project
Related Project Secure Score
Guess you like
Beosin KYT Analysis of Virtual Currency Addresses Associated with Hamas Sanctions
November 03, 2023

Beosin Research | Risks in Flashloans in Solidity
November 07, 2023

What security issues should developers consider when building Solana projects?
November 09, 2023

The Booming BTC Ecosystem: Exploring Opportunities and Risks in Derivative Protocols
November 13, 2023
