November 01, 2023
Focusing on EVM and Cosmos SDK chains, Beosin provides security services for the Celestia ecosystem

Celestia, a modular blockchain focused on data availability, is about to be launched and modular blockchains have become a hot topic in the market once again. By decoupling public chain functions, Celestia mainly assumes the functions of consensus layer and data availability layer, providing a simpler and more flexible solution for building decentralized applications and blockchains.
In this article, we will analyze Celestia's architecture and technology in detail to help you understand Celestia and its ecological development, as well as explain the best practices to build applications on the Celestia and to strengthen the security of projects.
What is Celestia?
Celestia is a modular Layer1 whose job is to order transactions and verify if the published data is available. The core concept of Celestia is to implement a modular blockchain architecture, so that developers can get rid of the limitations of a single architecture during the development process of building a blockchain.
Celestia's modularity is divided into execution layer, settlement layer, and consensus and data availability layer, as shown in the following figure:
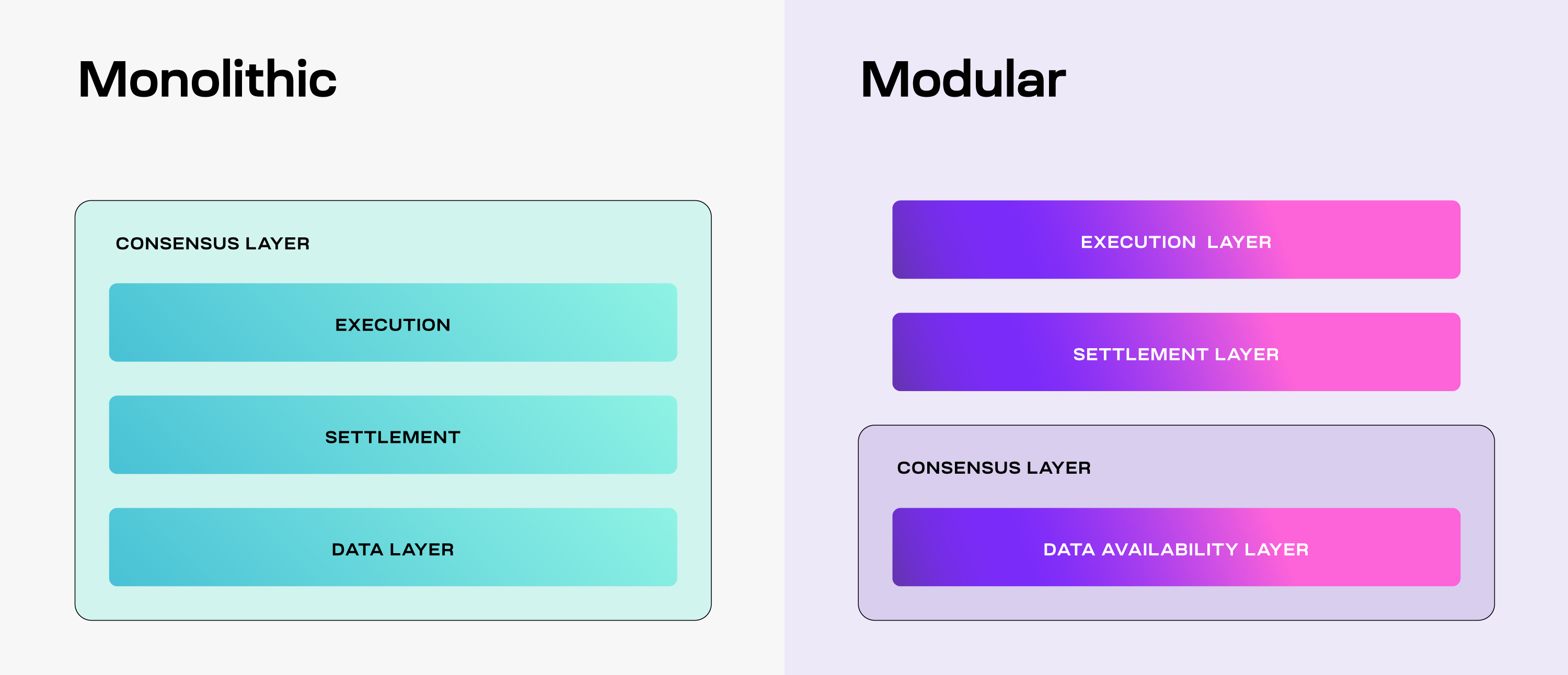
1. Execution layer
It is composed of Rollups and responsible for executing transactions. Celestia uses Rollups to provide diverse options for the execution layer. In addition to supporting Optimistic Rollup and zkRollup, Rollup solutions such as dYmension, Eclipse, and Fuel built based on Celestia make it possible to connect Cosmos and Solana ecosystem.
2. Settlement layer
What is currently worthy of attention is the settlement layer Cevmos developed by Celestia in cooperation with Evmos. It will build the recursive Rollup of EVM based on Evmos. Each Rollup built on Cevmos has a two-way bridge with Cevmos, which can redeploy existing Rollup contracts and applications on Ethereum, reducing the workload required for application migration.
3. Consensus and data availability layer
This layer is responsible for data availability and consensus mechanism. Data in all formats will be delivered to the data availability layer. The system incentivizes nodes to store data through TIA token and nodes use Reed-Solomon encoding and specialized Namespaced Merkle Trees to ensure data availability.
Celestia Security Practices
Due to its modular architecture, Celestia supports multiple programming languages and virtual machines, such as Solidity and Rust (CosmWasm), at both the settlement and execution layers. The modular feature of Celestia means that developers are not limited to these languages. They can use any existing languages and virtual machines, or even define their own languages and virtual machines, such as FuelVM and its programming language Sway.
Solidity best security practices
If you develop an application on Cevmos or other Rollup that supports EVM, the development process and required tools are almost identical to those on Ethereum, and the application can also be migrated to other EVM-compatible public chains. Following the following security guidelines can improve your project’s contract security:
1. All smart contracts may have vulnerabilities
For Cevmos or new Rollups that support EVM, the problem of contract vulnerabilities cannot be ignored. Therefore, when the project team develops the contract, it should set up an emergency pause function in the contract and formulate a risk response plan to quickly respond and repair vulnerabilities when risks arise.
2. Solidity does not have floating point numbers
When it comes to arithmetic operations, the accuracy of the results needs to be considered, especially when calculating the number and price of tokens. Developers should pay attention to the order of operations, use higher-precision data types such as uint256 to store variables, and then perform operations.
3. Contract upgrades
Developers should pay attention to the following points:
● Avoid calling external libraries in the deploy contract, because it is difficult to predict how external libraries will affect the contract's storage access.
● During the upgrade process, be careful not to overwrite the data of stored variables.
● Try to avoid doing anything in the constructor function.
4. Use multi-signature wallets
Project teams need to consider using multi-signature wallets to manage project treasury and smart contracts. Multi-signature accounts need to be held by multiple entities to avoid potential access control risks.
CosmWasm Security Practices
If developers plan to build applications on the Cosmos, they will use CosmWasm when developing smart contracts. Following the following security guidelines can improve the contract security:
1. Be prepared for potential attacks
Similar to developing contracts using Solidity, developers need to consider how to face attacks and fix vulnerabilities. Therefore, developers need to build upgradable smart contracts and develop risk response plans.
2. Be aware of addr type deserialization
The addr type of CosmWasm is not validated during deserialization, which indicates that the addr type has unexpected deserialization characteristics. Therefore, it is recommended to specify the type and validate it after deserializing addr.
3. Be careful about arithmetic operations
In the CosmWasm contract, developers need to pay attention to the risk of integer overflow or division by zero. It is recommended that developers use CosmWasm Uint256 and Uint512 types and use the math function full_mul() that does not overflow.
4. Avoid infinite loop
The CosmWasm contract may get stuck in an infinite loop by calling itself back in the ACK handler if developers transfer data packets between two CosmWasm contracts. They should be aware that an infinite loop will consume a large amount of gas fees.
Protocol Security Practices
1. Smart contract audit
Smart contract audit is to systematically test and review the smart contract code to discover potential security loopholes as much as possible, eliminate security risks, and ensure that the code has no business logic loopholes and conforms to the expected operating process and results. Regular security audits of the project's smart contracts are crucial. It is recommended that the audit be conducted after the contract development is completed and before the mainnet is deployed.
As a world-leading blockchain security team, Beosin focuses on blockchain security and formal verification technologies, provides detailed and comprehensive security audits for EVM and Cosmos ecological applications, and is committed to providing advanced solutions for the entire blockchain ecosystem. Safety and security. Previously, Beosin has completed the security audit of Kryptonite, the largest liquidity staking protocol in the Cosmos public chain Sei ecosystem, to protect Sei's staking services.
2. Formal verification
Formal verification is different from security auditing. It is based on strict mathematical proofs and provides complete coverage of the program to prove that the code implementation meets security or functional requirements.
Beosin takes full advantage of the wide application range of static analysis and the high accuracy of dynamic analysis, and uses the self-developed high-performance Beosin VaaS, a formal verification tool to automatically perform formal verification of smart contract codes to discover things that are difficult to discover in pure manual audits or traditional testing.
Summary
Celestia is a modular Layer1 with great potential, featuring scalability, flexibility and interoperability. Currently, Celestia's ecosystem is still in the early stages. While exploring modular solutions, developers can effectively improve project security by following the above security practices.
Beosin is a leading global blockchain security company co-founded by professors from world-renowned universities and there are 40+ PhDs in the team. It has offices in Singapore, Hong Kong, Japan and other 10+ countries and regions. With the mission of "Securing Blockchain Ecosystem", Beosin provides "All-in-One" blockchain security solution covering Smart Contract Audit, On-chain Risk Monitoring & Alert, KYT AML, and Crypto Tracing. Beosin has already audited more than 3000 smart contracts including famous Web3 projects PancakeSwap, DODO, DeBox and Ankr and all of them are monitored by Beosin EagleEye. The KYT AML are serving 100+ institutions including Hashkey, Cobo, OpenBlock, Aegis and Celer.
Contact
If you need any blockchain security services, welcome to contact us:
Related Project
Related Project Secure Score
Guess you like
Blockchain Security Recap of October: $51.61M Lost in Attacks
November 01, 2023
Beosin KYT Analysis of Virtual Currency Addresses Associated with Hamas Sanctions
November 03, 2023
Analysis of $2.18 Million Loss in Hacker Attack on OnyxProtocol
November 03, 2023

Beosin Research | Risks in Flashloans in Solidity
November 07, 2023
