November 14, 2023
Poloniex under Justin Sun Hacked for Over a Billion Dollars, Raft Project Loses $3.4 Million

Last week witnessed two significant security incidents.
Firstly, around 19:00 UTC+8 on November 10, Beosin EagleEye detected continuous large asset outflows from addresses related to Poloniex under Justin Sun’s control, indicating a possible theft.
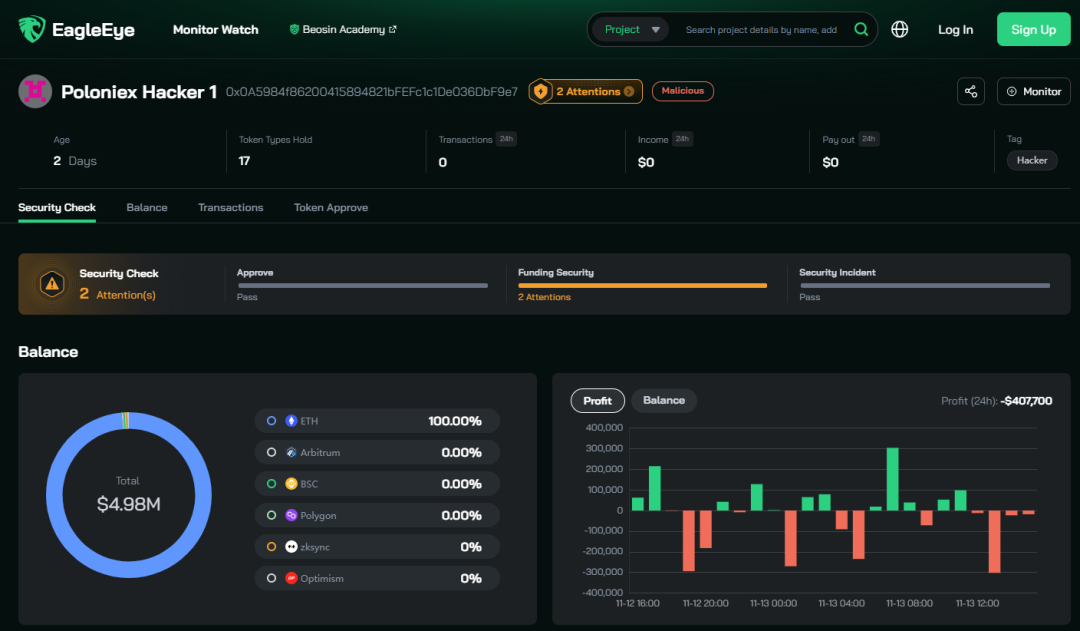
Shortly after, Justin Sun and Poloniex confirmed the theft through announcements on social platforms. According to Beosin security team, utilizing Beosin Trace for tracking and statistics, the accumulated stolen assets from Poloniex amounted to approximately $114 million.
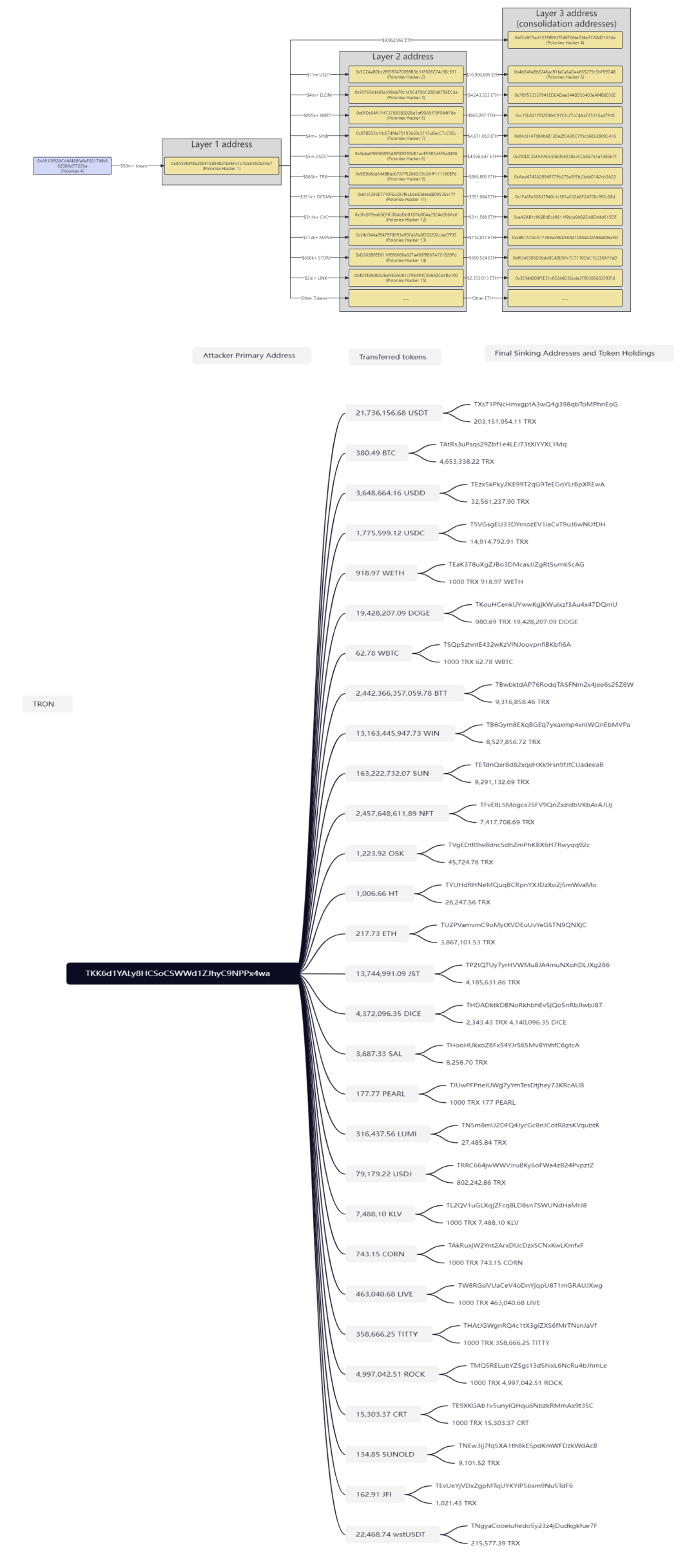
The hacker dispersed stolen tokens to various addresses for conversion and deposited them into different addresses. By around 20:30 on November 10, the attacker had converted stolen tokens into over $30 million worth of ETH on the Ethereum chain and over $20 million worth of TRX on the TRON chain. Simultaneously, the ongoing conversion and transfer of funds continued. The detailed transaction information is illustrated in the following graph.
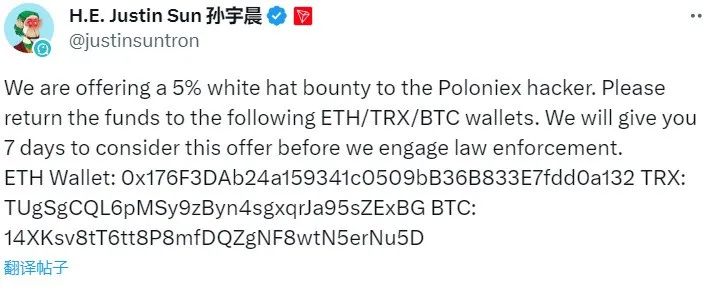
After the attack, Justin Sun appealed to the hacker to “refund” quickly, offering a 5% asset reward as a white-hat incentive. However, the hacker did not respond.
Coincidentally, on the next day, November 11, 2023, Beosin EagleEye platform detected a hack on the IRPM contract of the Raft project on the Ethereum chain, resulting in a loss of approximately $3,407,751. The attack was quite complex, and Beosin security team will share a detailed analysis of the results.
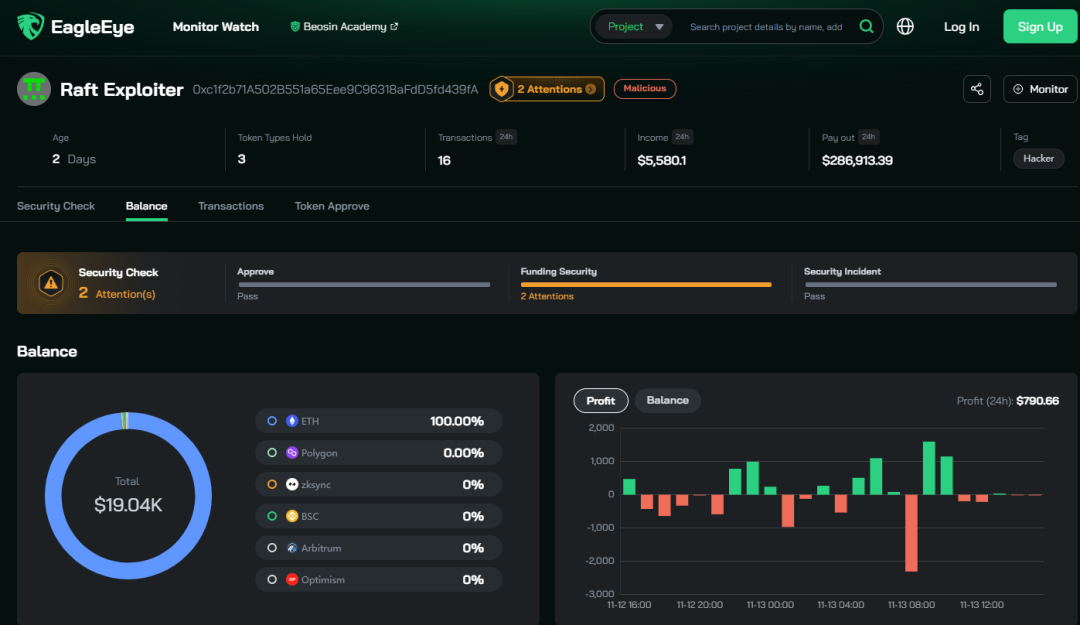
Raft Project Security Incident Details
Attacking Transaction:
0xfeedbf51b4e2338e38171f6e19501327294ab1907ab44cfd2d7e7336c975ace7
Attacker’s Address:
0xc1f2b71A502B551a65Eee9C96318aFdD5fd439fA
Attack Contract:
0x0A3340129816a86b62b7eafD61427f743c315ef8
Attacked Contract:
0x9ab6b21cdf116f611110b048987e58894786c244
Raft Project Security Incident Vulnerability Analysis
The attacker mainly exploited the manipulation of the collateralization ratio using flash loans. The coin minting calculation adopted rounding up, and the attacker leveraged the manipulated collateralization ratio to amplify the impact of rounding up, enabling borrowing a significant amount of assets with minimal collateral.
Attack Process
Preparation Phase:
- The attacker borrowed 6001 cbETH using a flash loan in AAVE through the attack contract for manipulating interest rates.
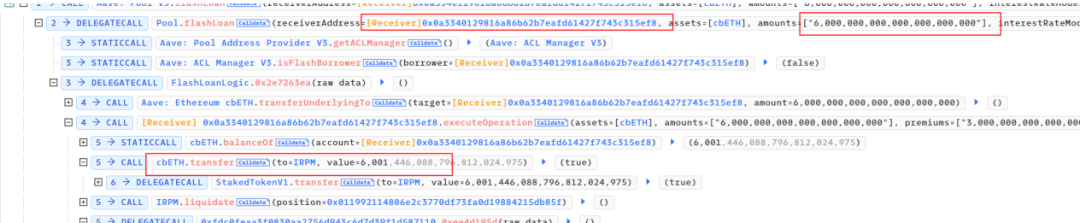
The attacker liquidated their own borrowings on IRPM.
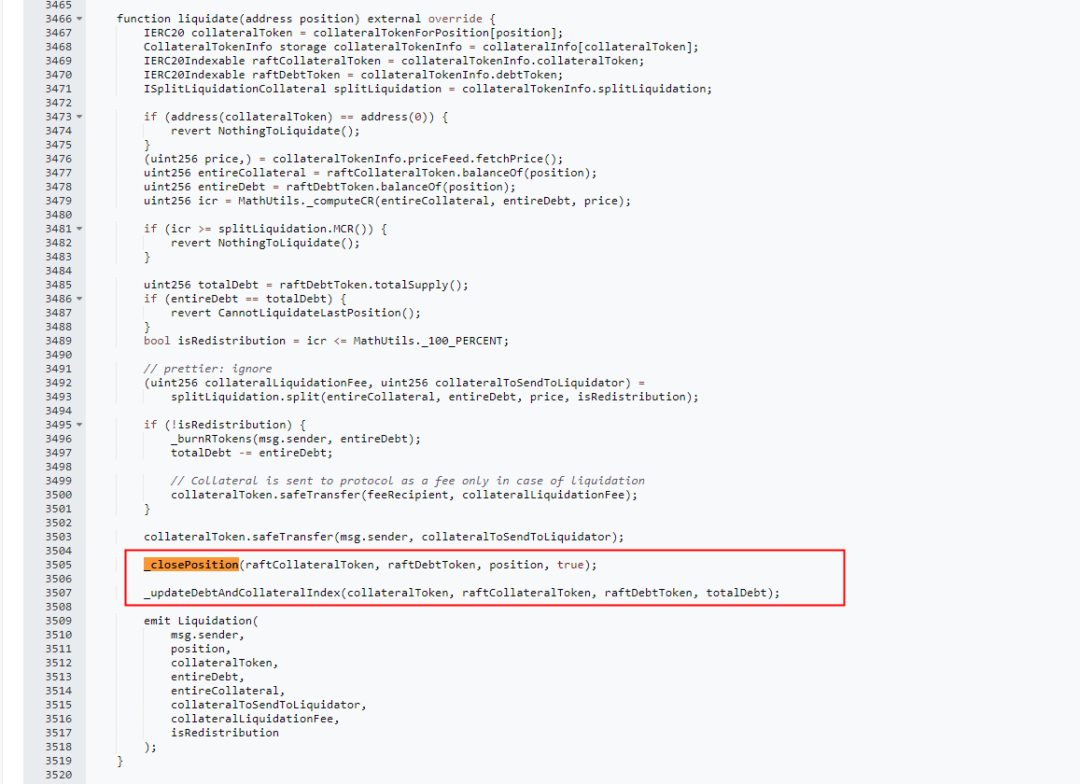
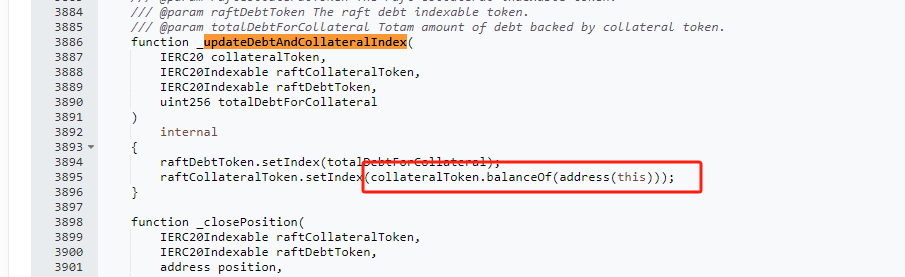
The attacker conducted a two-phase liquidation. In the _closePosition function, the attacker burned half of the quantity of rcbETH-d (rcbETH-d represents the debt token of the Raft project, rcbETH-c represents the collateral asset token).
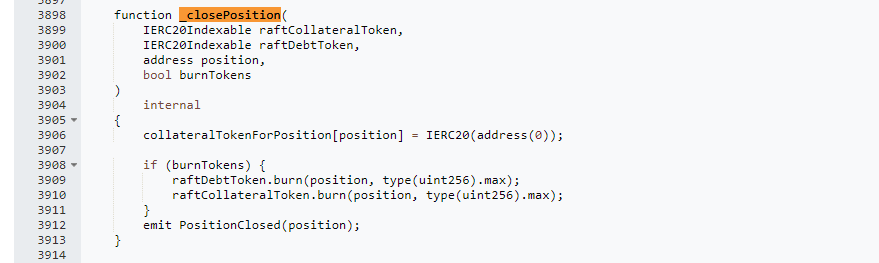
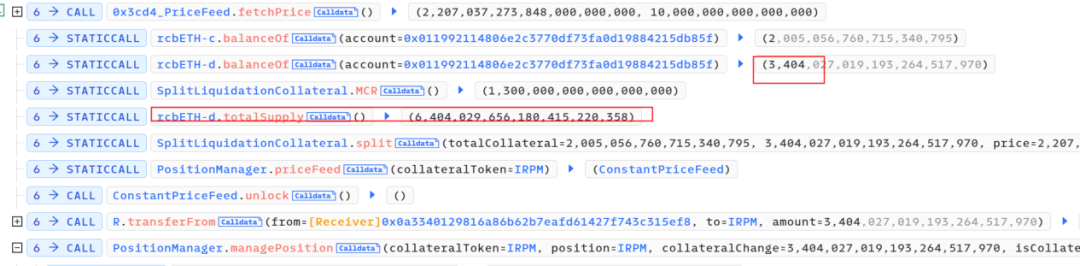
After the _closePosition function, the second phase called _updateDebtAndCollateralIndex to update the new lending rate.
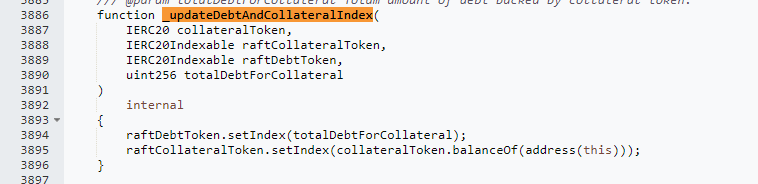

The total debt amount was halved due to the previous liquidation.
Due to the utilization of balanceof(address.This) as a parameter in the interest rate update of the collateral asset raftCollateralToken.setIndex, the attacker gained control by directly transferring the 6001 cbETH borrowed through a flash loan into the contract. It can be observed that out of these 6003 cbETH, 6001 remained unaltered.
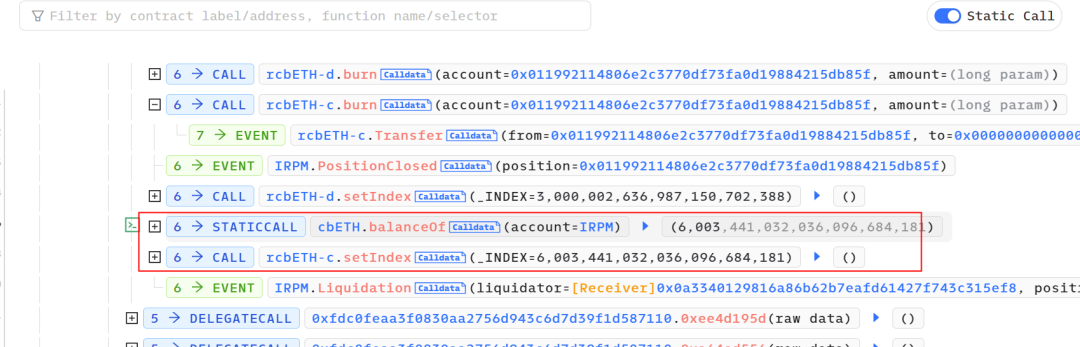
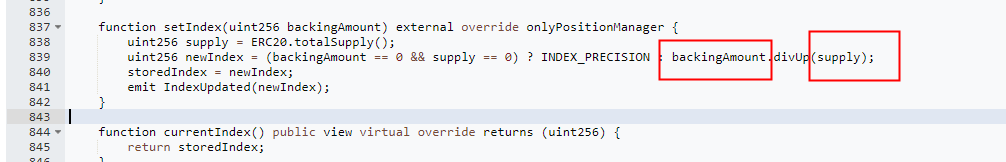
In the setIndex function of the cbETH token, although there is permission control, the new interest rate is calculated by the attacker-controlled backingAmount divided by the total token quantity. The attacker exploited the permissions of the attacked contract (IRPM) and supplied abnormal parameters, causing the storedIndex to inflate to 6710³⁶ (increased by 6710¹⁸).
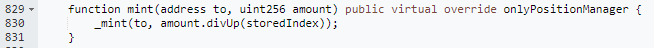
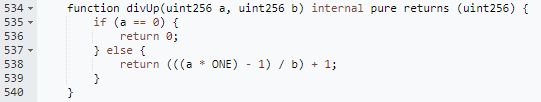
2. After manipulating the collateralization ratio, the attacker, through another attack contract 0xfdc0feaam, conducted multiple minting operations of cbETH to produce rcbETH-c. The minting function here utilizes rounding up. Since the storedIndex was inflated by 6710¹⁸, the minting quantity would be reduced by a factor of 6710¹⁸. However, due to the rounding-up method employed in the minting function, what should have been a 1:1/(6710¹⁸) ratio turned into a 1:1 minting, effectively amplifying the collateral value by 6710¹⁸.
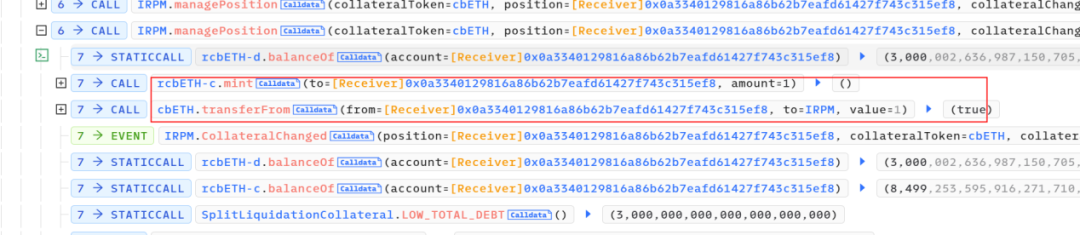
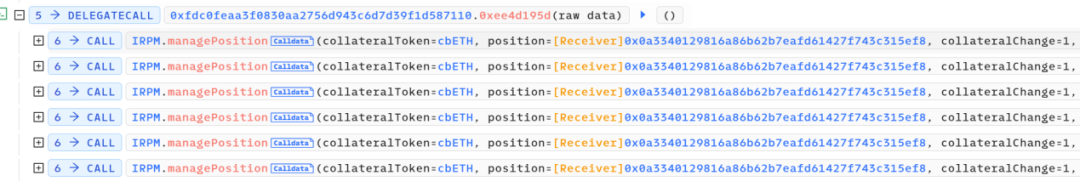


3. After multiple minting operations, the attacker obtained 10,050 rcbETH-c and initiated borrowing. The accumulated debt quantity, rcbETH-d, remained constant at 3000.
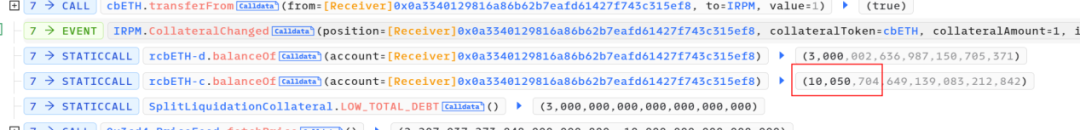
4. Subsequently, after accumulating a substantial amount of rcbETH-c, the attacker borrowed the funds required to repay the flash loan.
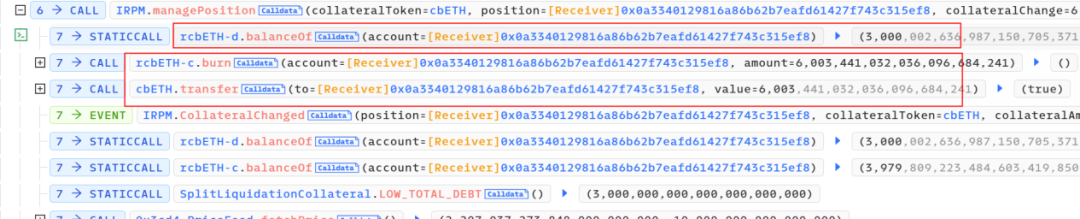
They then borrowed a total of 6,705,028 R tokens and converted 3,300,000 R tokens, ultimately receiving 1575 ETH. However, during the conversion, the ETH was sent to address 0x0.
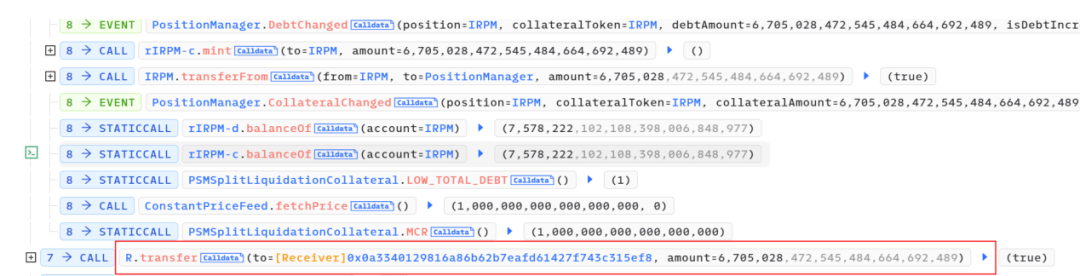
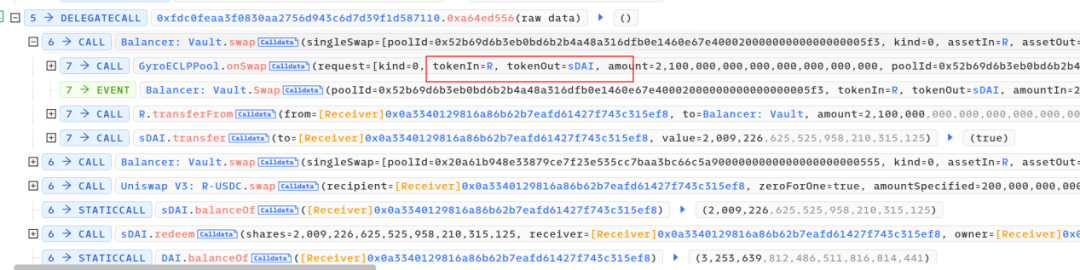
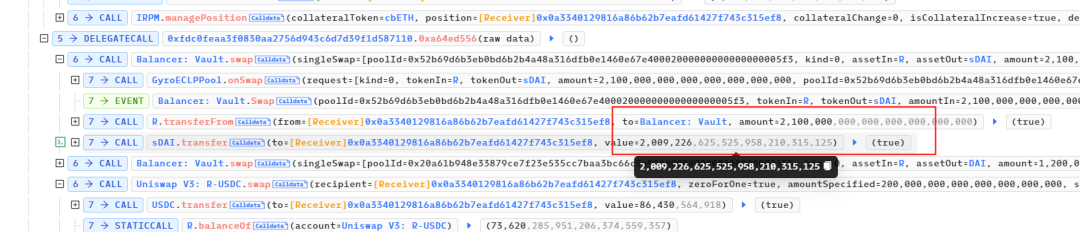
The remaining 3,322,460 R tokens left 1,442,460 in the account. The remaining 1,900,000 R tokens were transferred to the attack contract, exchanging for an additional 127 ETH.
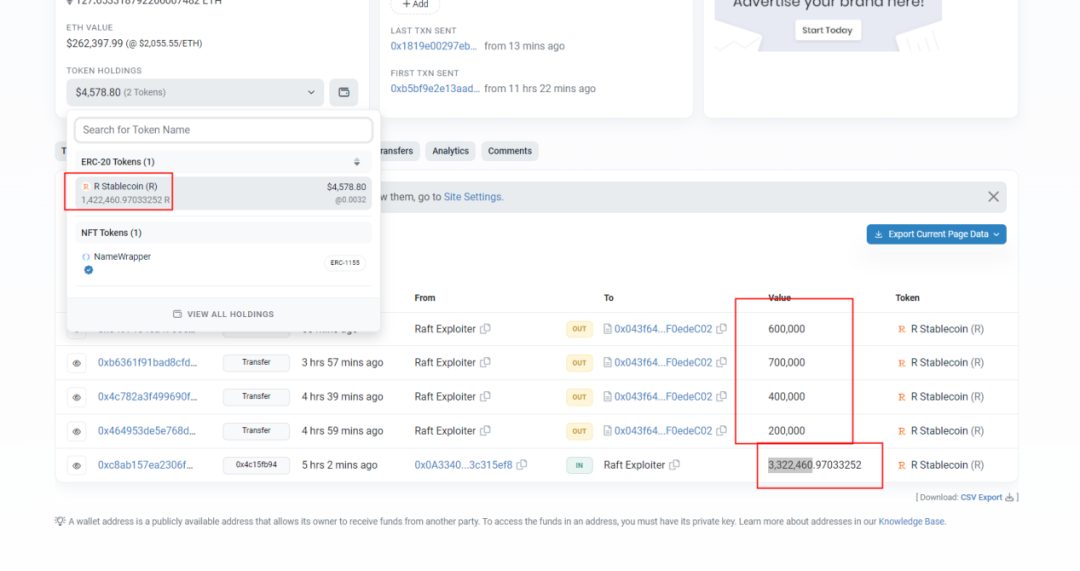
Funds Tracing in Raft Project Security Incident
As of the time of this post, the IRPM contract of the Raft project has incurred a total loss of $3,407,751. Among this, Ethereum (ETH) valued at $3,140,000 was inadvertently transferred by the attacker to the address 0x0. The remaining profits were gradually liquidated by the attack contract, resulting in $267,751 being sold in batches.

Conclusion
For the Poloniex security incident, Beosin advises wallets or projects to safeguard private keys. Regarding the Raft project IRPM contract security incident, Beosin security team suggests:
1. Critical functions like collateralization ratios should use oracle quotes for calculation.
2. Coefficient calculations should multiply before dividing, and avoid using rounding-up methods whenever possible.
3. Additionally, it is recommended that projects seek professional security auditing companies for comprehensive security audits before going live.
Contact
If you need any blockchain security services, welcome to contact us:
Official Website Beosin EagleEye Twitter Telegram LinkedIn
Related Project
Related Project Secure Score
Guess you like

The Booming BTC Ecosystem: Exploring Opportunities and Risks in Derivative Protocols
November 13, 2023

How to Identify Cryptocurrency Traps? EagleEye Deciphers the Schemes
November 20, 2023

Beosin Unveils New Blockchain Solution for Financial Regulation and Security at SFF
November 20, 2023

A Security Perspective on the GameFi Fren Pet Across the Entire Chain
November 23, 2023
